Wallet creation
Onboarding #
Now that we have a good understanding of how Bob and Alice want to set up their inheritance wallet, let’s take a close look at the first use experience and wallet setup.
After downloading the app, it walks them through the purpose of the product and highlights some of the most important features.
Onboarding begins with a short video that explains what the application is all about.
It also emphasizes the social aspect of having shared inheritance wallet.
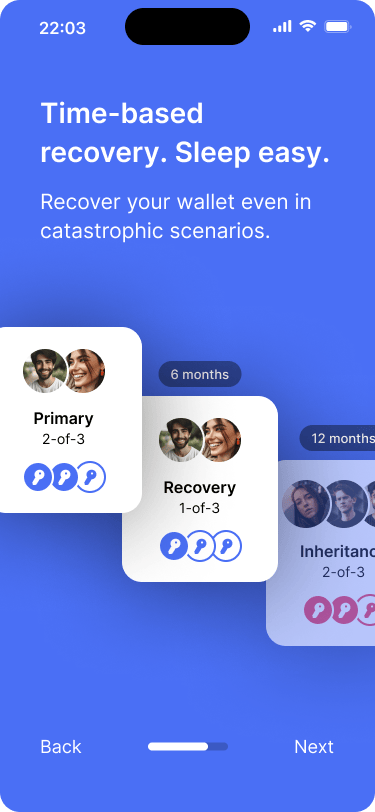
One of the main features is that it’s very easy to create time-based recovery options.
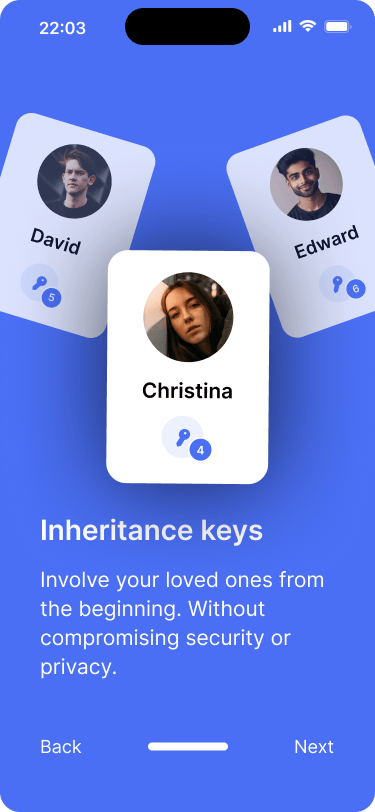
Heirs can be involved from the beginning and provide their own inheritance keys.

The tutorial finishes with a call to action.
Wallet creation #
After going through the app onboarding flow, Bob and Alice are ready to create their savings wallet. The wallet creation flow consists of three main tasks:
- Configure the wallet
- Import the signing keys
- Review and finalize the wallet
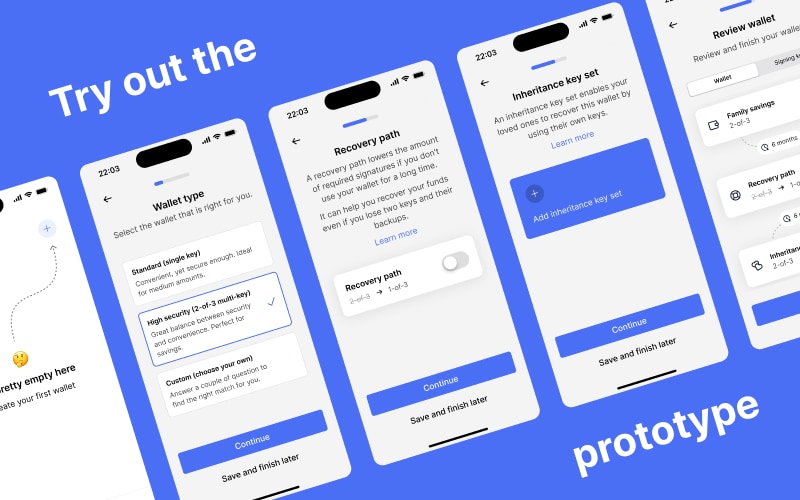
Try out the prototype below. It covers the entire wallet creation process.
Step 1: Wallet configuration #
We start with wallet configuration, where Bob and Alice define the rules for how the wallet should work. In the second part, they add all the signing keys.
Creating the primary key set #
Bob starts the wallet creation process on his phone, while Alice will use the app on her own phone to add her signing key. The app gives them a choice between two of the most commonly used wallet types: The first one is a standard, single-key wallet. The second option is a 2-of-3 multi-key wallet, which is suited for larger savings. There is also a third option that allows users to create their own custom setups. Bob and Alice choose the 2-of-3 multi-key wallet.
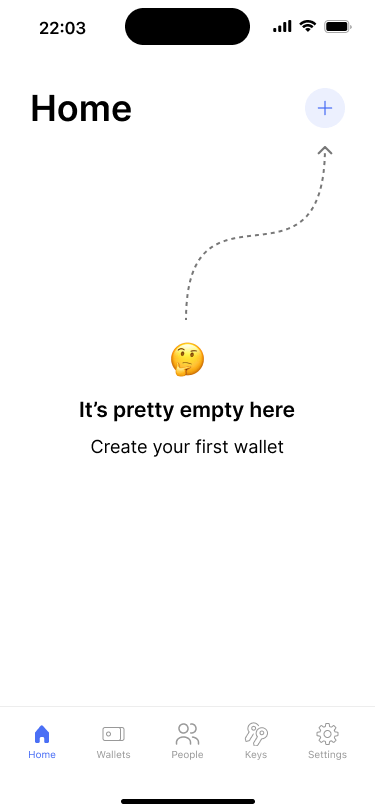
The empty state of the home screen prompts users to add their first wallet.
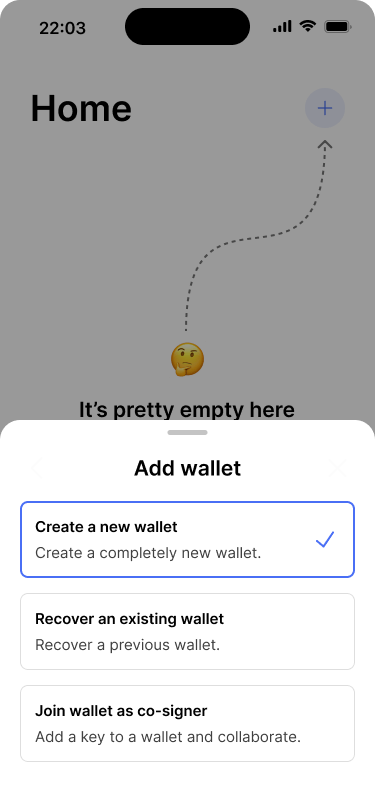
Users can choose to create a new wallet, recover an existing one or join wallet as a co-signer.
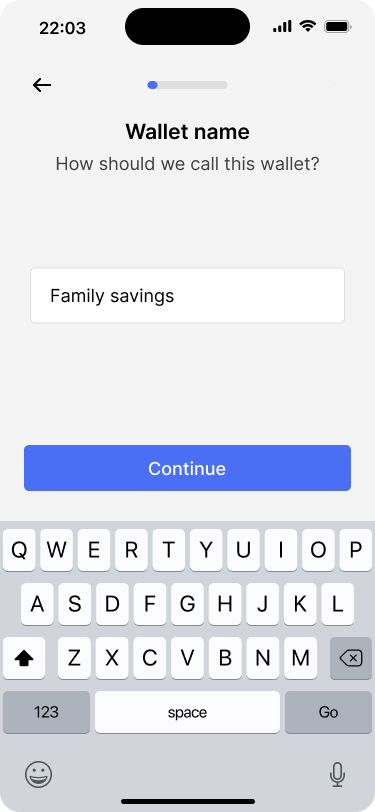
Users can give their wallet a friendly name.
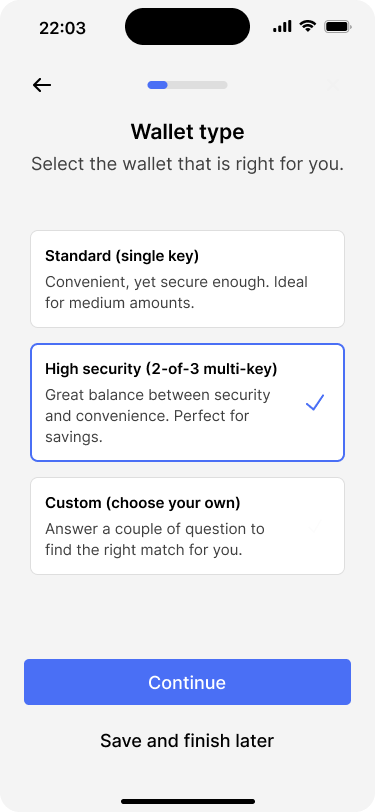
Users can choose between common wallet types or create their own custom configuration.
Enabling the recovery path #
After configuring the primary key set, the app asks the users whether they would like to enable a recovery path. The recovery path uses the same keys that are part of the primary key set and unlocks after 6 months of inactivity. If it is unlocked, only one signature will be required to spend bitcoin, instead of two. We have covered this in the time-based recovery reference design as well.
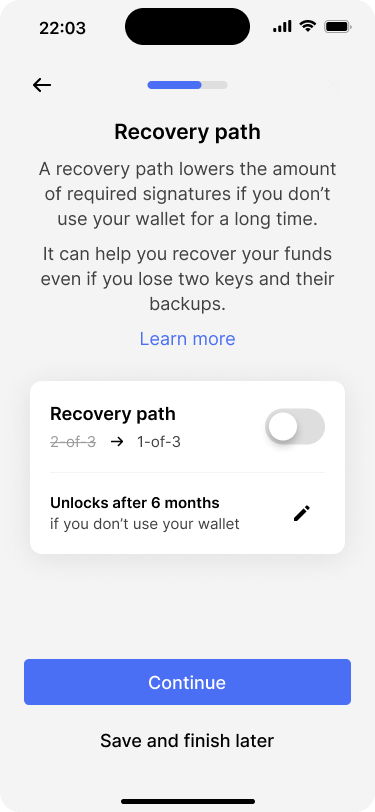
Users can choose to enable the recovery path.
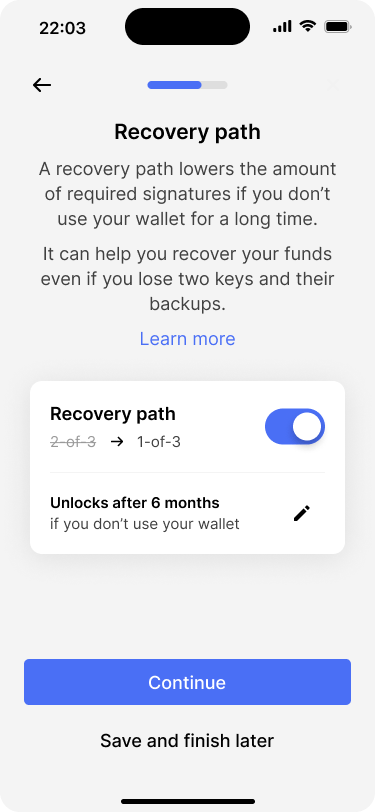
By default, the recovery path will be unlocked after a delay of 6 months. Users can edit this setting.
Creating the inheritance key set #
After enabling the recovery path, the app offers users to create a dedicated inheritance key set. The process of configuring the key set is almost the same as for the primary key set.
The main difference is that the inheritance key set should only be unlocked after a certain amount of time. Therefore, Bob is prompted to define the rules under which the key set should be unlocked, after he has chosen the appropriate key set type.
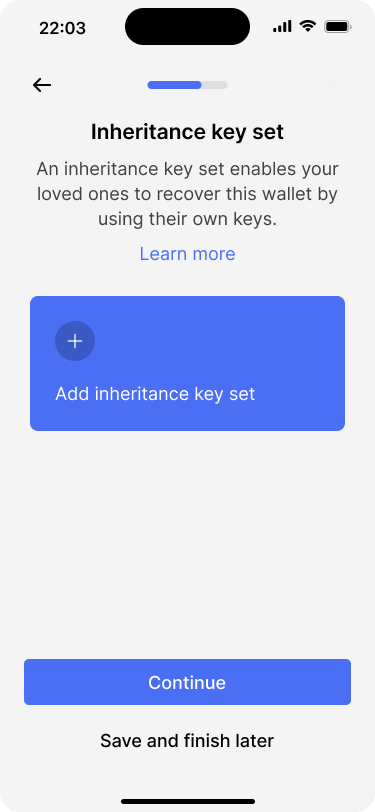
The inheritance key set is optional and could also be skipped.
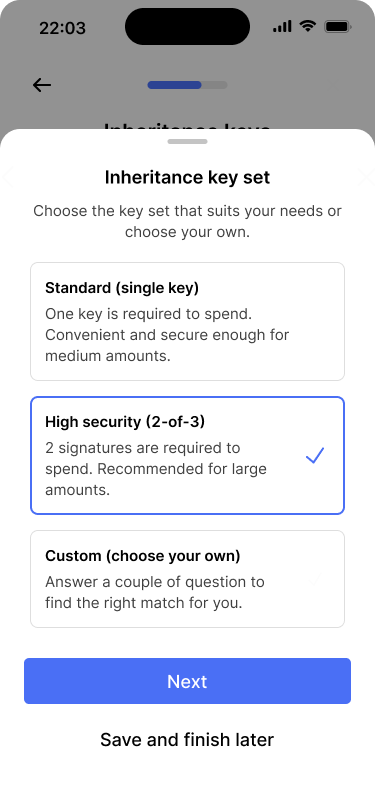
Users can choose between common wallet types or create their own custom configuration.
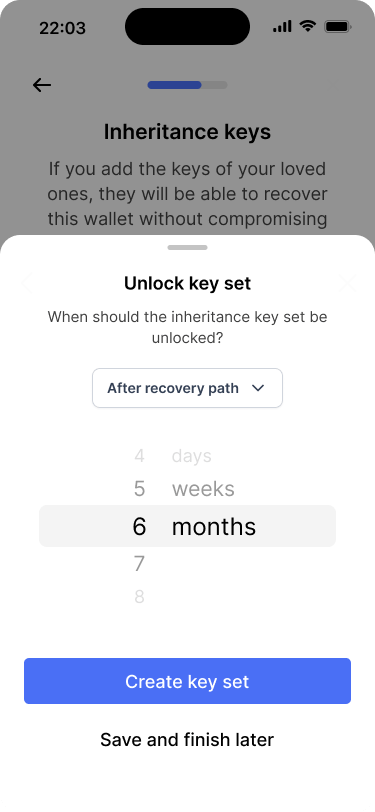
Users can configure the timing of when the inheritance key set should be unlocked.
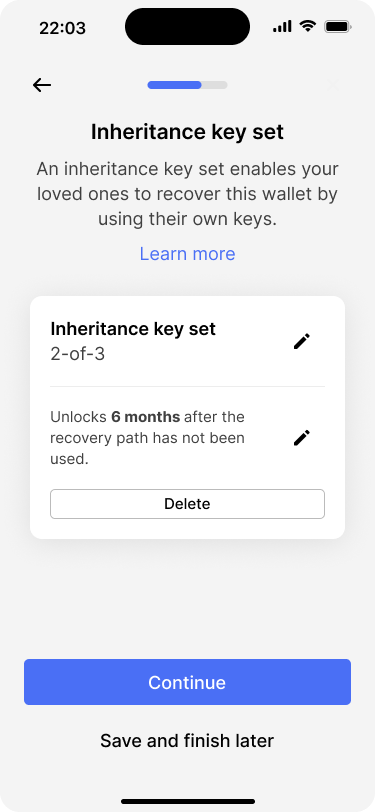
The app shows an overview of the inheritance key set configuration. Users can edit or delete the key set.
Step 2: Adding the signing keys #
The wallet is now fully configured. What is left to do is to add the signing keys. Adding a key technically means that users have to import the extended public key (XPUB) from each signing device that should be used to sign transactions.
Adding the primary keys #
This sounds more complicated than it actually is. Depending on the specific signing devices that are being used, it can be as simple as scanning a QR code, connecting it via NFC or Bluetooth, or by using a USB cable.
Bob adds the first two keys #
Bob gets started and imports the first two keys by himself. One from his personal Trezor and one from a Coldcard that he shares with Alice.
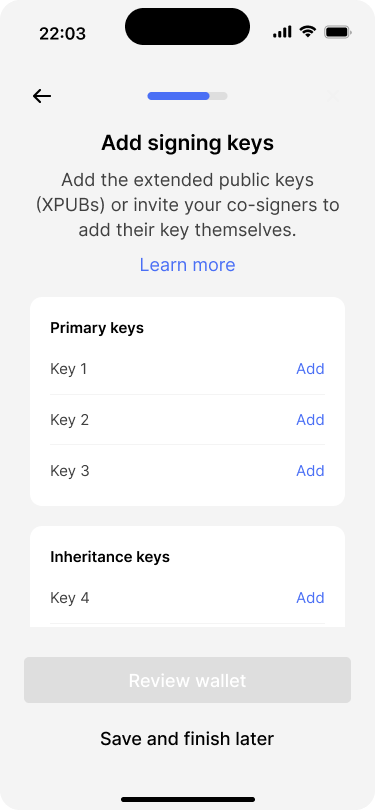
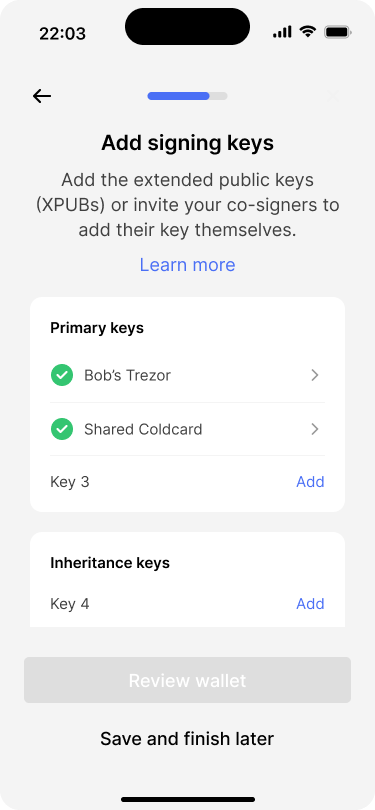
Based on the wallet configuration, the app shows one empty slot for each key that needs to be added.
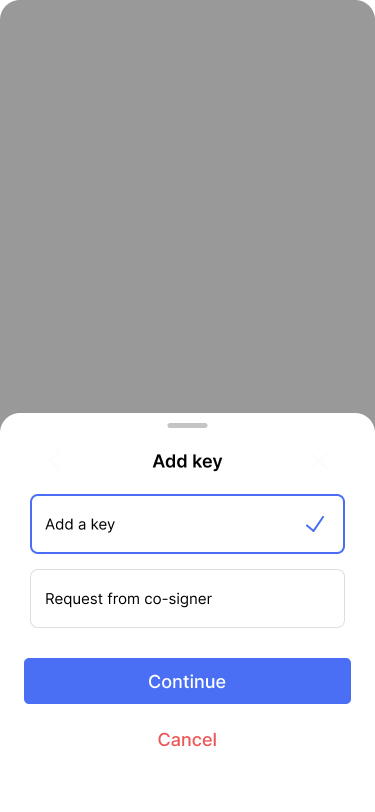
Users can add a key themselves or request it from the designated cosigner.
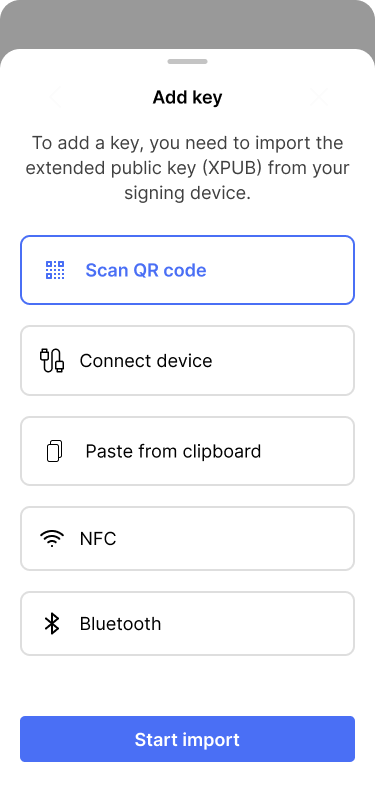
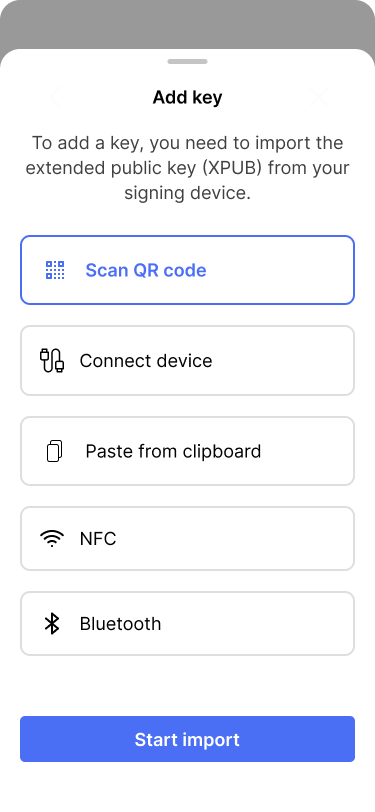
Users can choose from a variety of options to import the extended public key.
The import flow depends on the specific hardware device and import method being used.
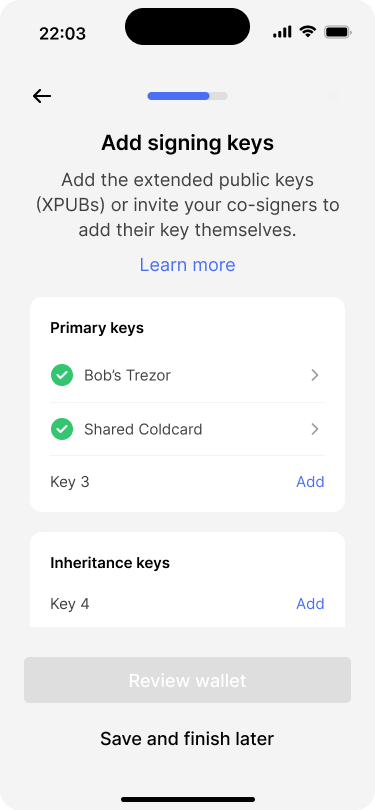
Two out of six keys have been imported. The user can tap on any key to view its details.
Bob requests the third key from Alice #
Next, it’s time to add Alice’s key, which will be imported from her BitBox. Our app makes this process easy, because Bob can just create a key request that Alice can scan with her phone. Alternatively, he can also send it to her via a secure channel.

Two out of six keys have been imported. Bob adds the third key.
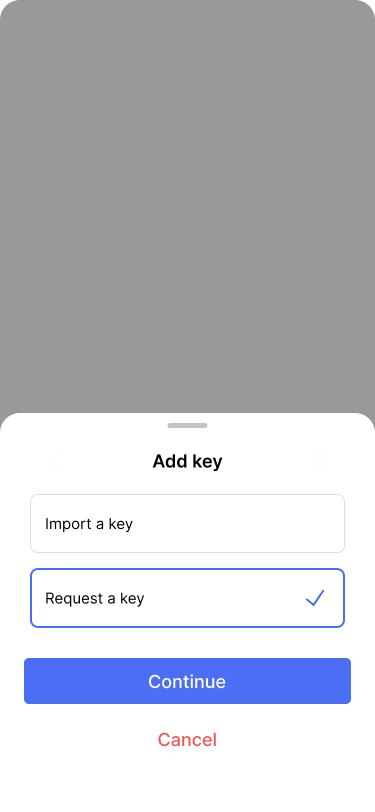
Bob would like to request the third key from Alice.
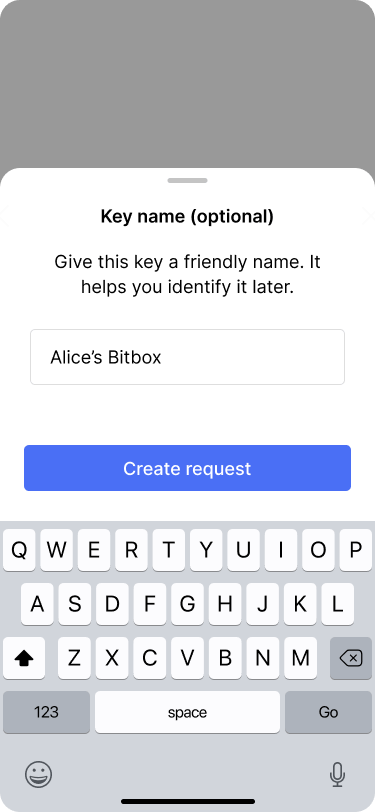
Bob gives this key a friendly name, so that it can be identified later on.
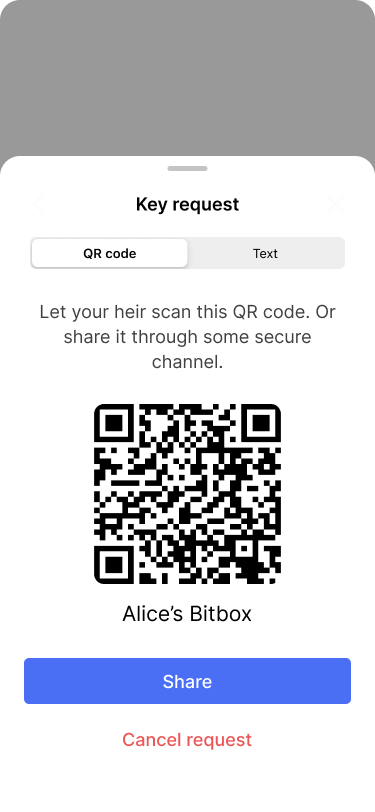
The app generates a QR code that can be scanned to import the key. The request can also be shared via native sharing options of the operating system.
Alice imports the key from her signing device #
Alice has also downloaded the app, so she taps the big plus button on the homescreen and selects “provide a key” from the menu that pops up. On the next screen, she chooses to scan the key request. After doing that, the app displays the wallet configuration. Alice sees that her key will be used in the primary key set. She taps “provide key” and the app takes her through the same process like Bob.
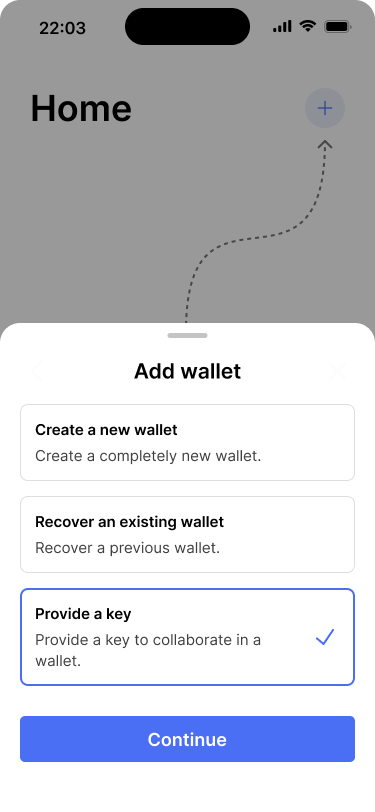
On her end, Alice selects “Provide a key” to add her key.
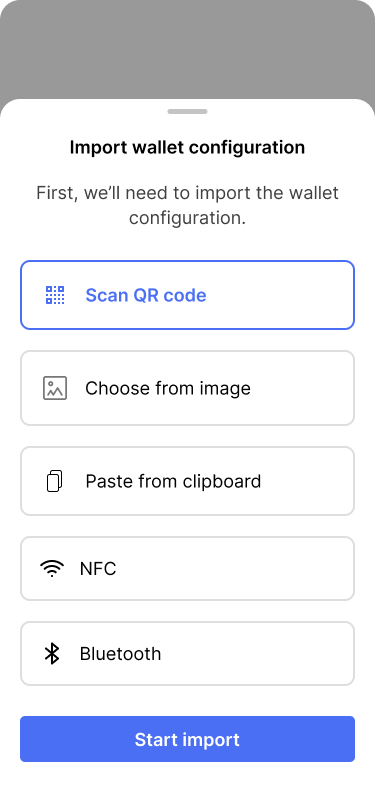
Alice chooses to scan the the wallet configuration from Bob’s screen.
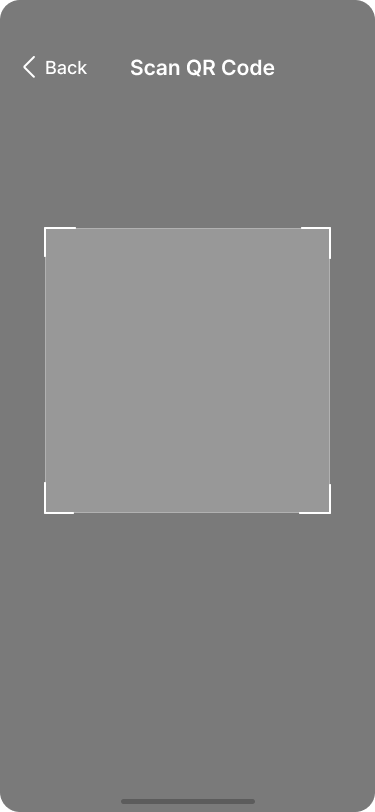
The app opens the QR code scanner to import the wallet configuration.
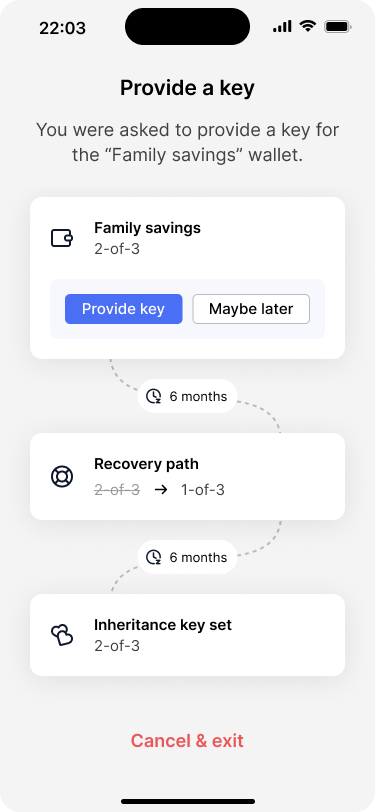
The app shows the configuration of the wallet and shows Alice, in which key set her key will be used.
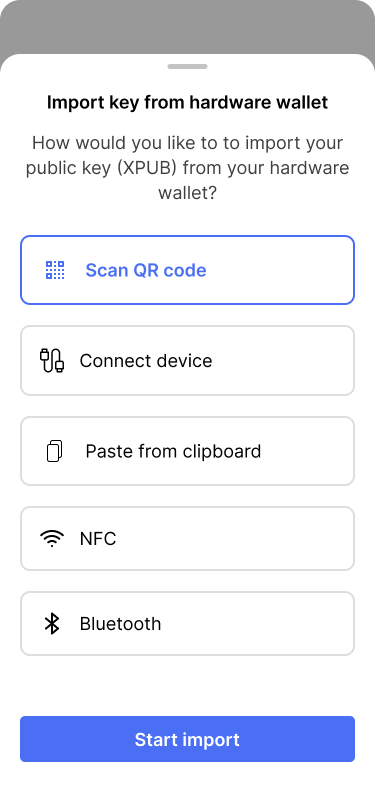
The app offers Alice different options to import her key.
The import flow depends on the specific hardware device and import method being used.
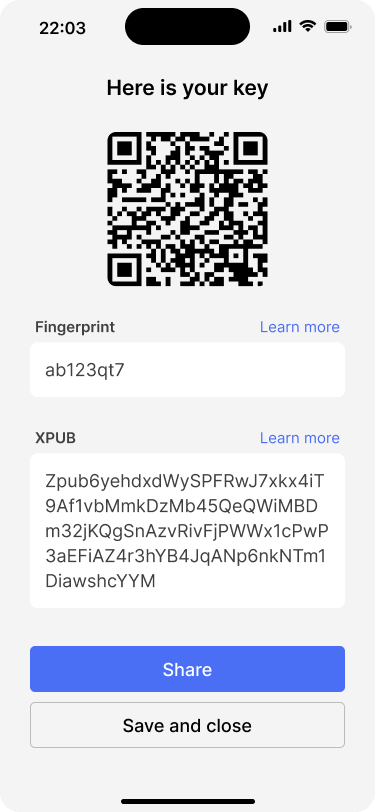
Alice checks the details of her XPUB against what is shown on her hardware device. The key can also be saved locally for later use.
Alice provides her key to Bob #
But there is one additional step to take: Alice needs to transfer the information about her key back to Bob, so that he can add it to the wallet configuration. Since they are in the same room together, Bob scans the QR code that is shown on Alice’s screen and goes through the same process as for the first two keys.
Bob adds the third primary key.
He chooses to import Alice’s key by scanning the QR code which is displayed on her screen.
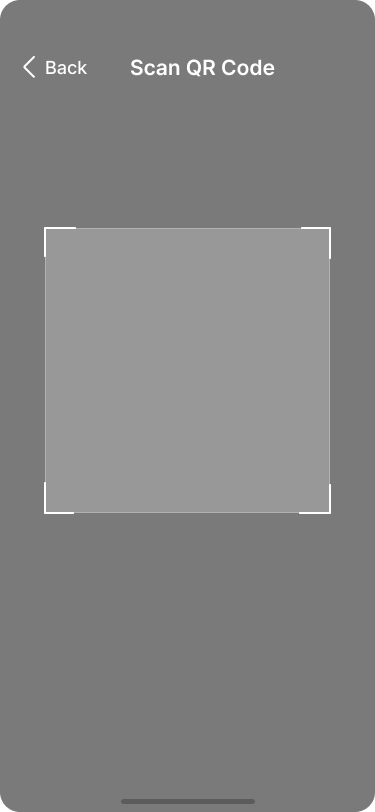
Bob scans the QR code.
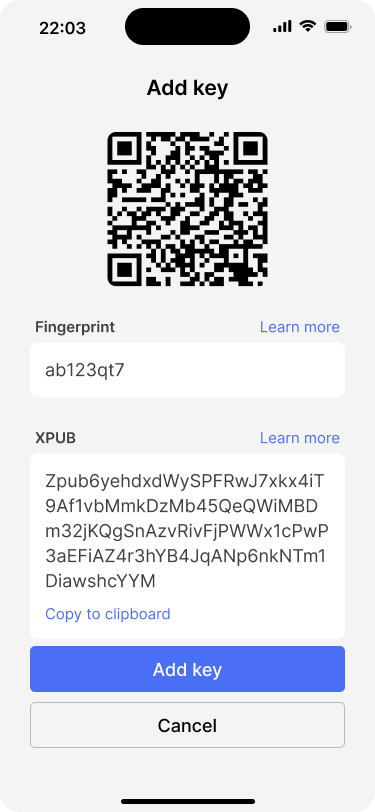
Bob reviews the XPUB and adds it to the wallet.
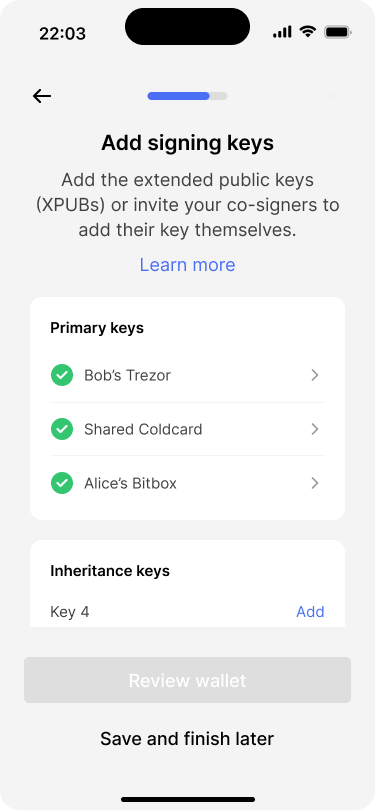
Alice’s key has been added to the wallet.
Time to hit pause #
All primary keys have now been added to the wallet. Next, Bob and Alice need to add the inheritance keys in the same way. They plan to do that during a family gathering which is coming up on the following weekend. For now, Bob hits “Save and finish later”. The application saves the progress locally and allows Bob to continue later.
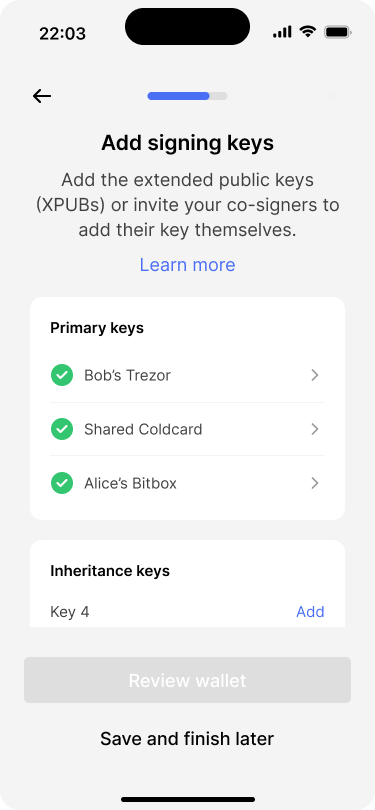
Bob taps “Save and finish later”. He will resume the wallet creation at a later time.
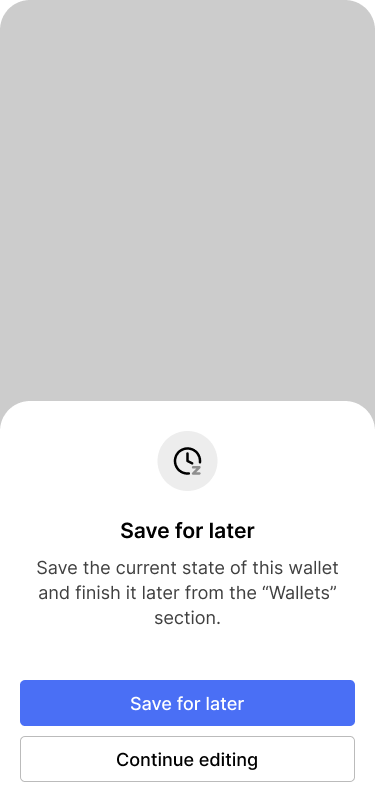
The app asks him to for confirmation.
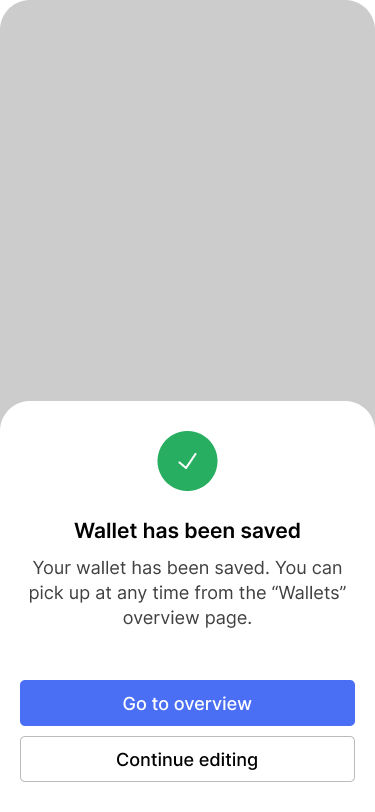
After saving the current state of the wallet configuration, Bob goes to the overview.
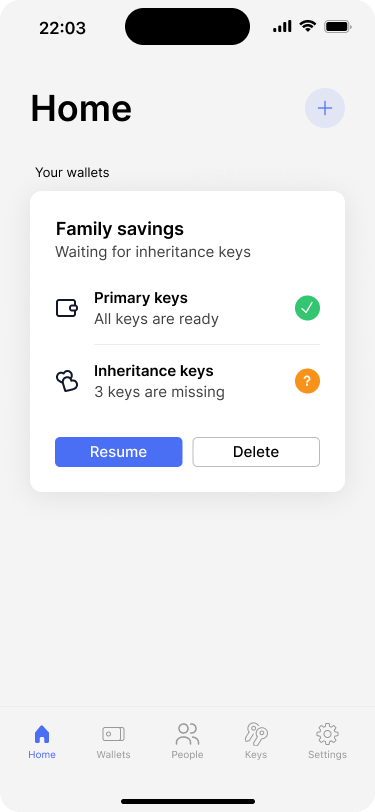
The app home screen shows the progress of the family savings wallet.
Adding the inheritance keys #
Bob and Alice already met with Edward, their lawyer, ahead of the family meeting and imported his key to the wallet. So only Christina’s and David’s keys remain to be added to the wallet.
During the family reunion, Bob opens our application and resumes the wallet creation process. Just like with Alice’s key, he creates a key request for Christina and David.
Christina creates a new key in the app #
Christina could follow the same procedure for importing a key from her existing signing device, as described above. However, Christina does not want to use her existing hardware wallet from the family savings. Instead, she wants to create a new key for the family savings wallet, so that she can keep it on a separate signing device.
The mockups below show how our app allows Christina to generate an entirely new key and provide it to her father.
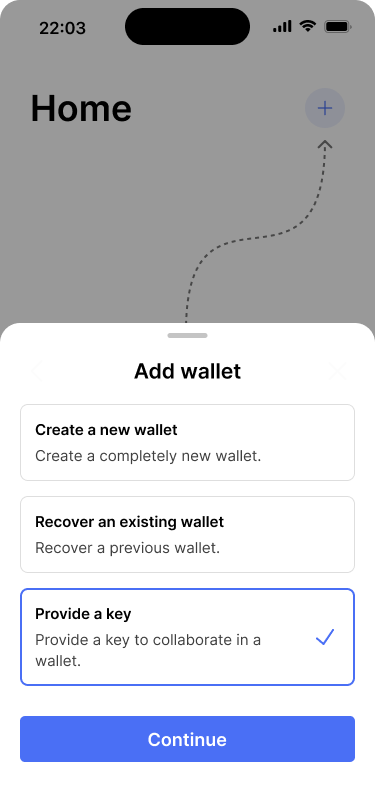
Christina starts to provide a key to the wallet.
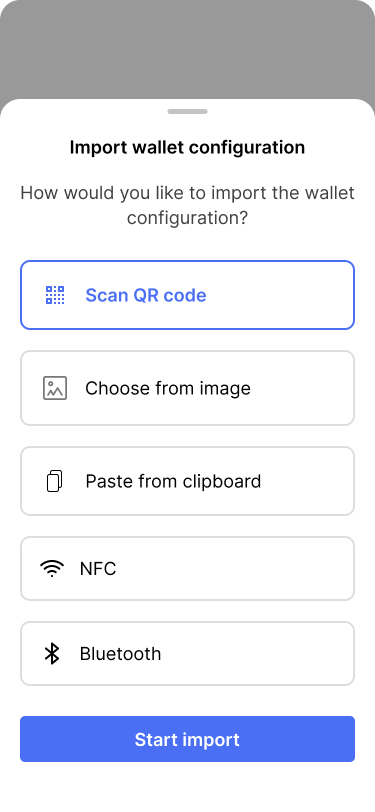
She chooses to import the wallet configuration by scanning the QR code.
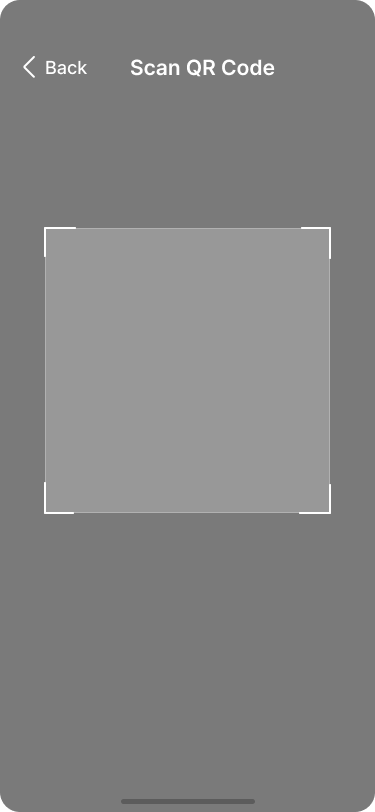
Christina scans the QR code her father has generated.
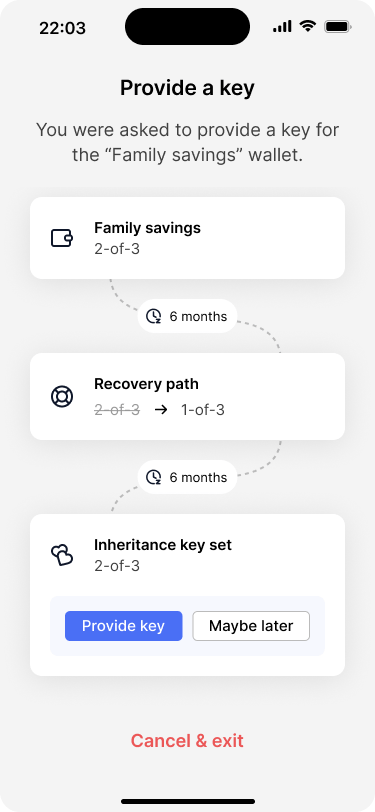
The wallet overview screen shows that Christina’s key will be part of the inheritance key set.
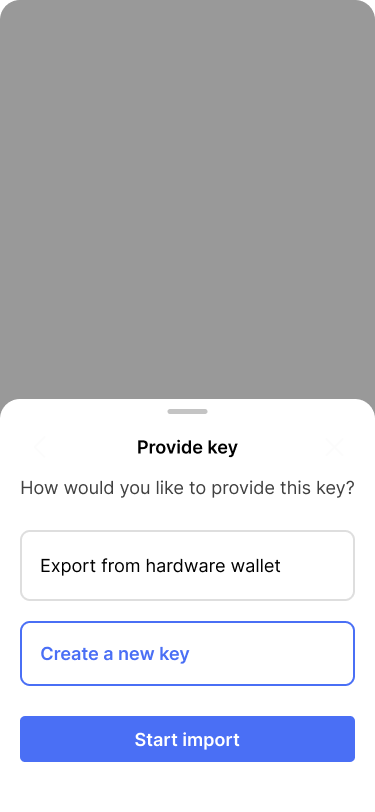
Christina chooses to create an entirely new key.
The application generates a new private key…
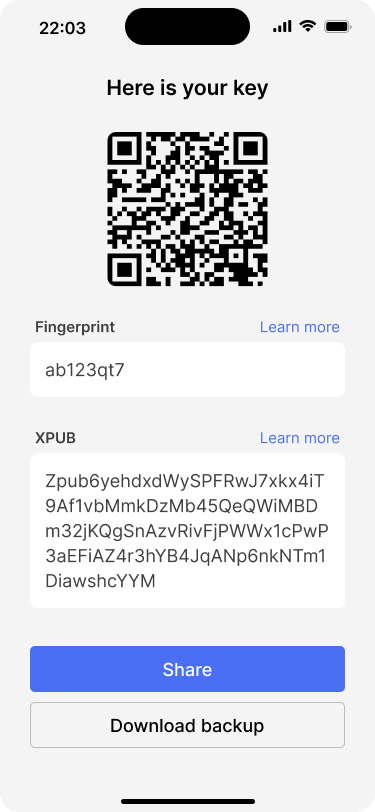
… and derives an extended public key from the newly generated private key.
David forgot his hardware wallet #
Unfortunately, David forgot his hardware wallet at home, so he will have to add his key later. So Bob creates the same request as usual and sends it to David via direct message. The user flow for David is the same as for Alice and Edward. The only difference is that he sends his key back to his father over a direct message as well.
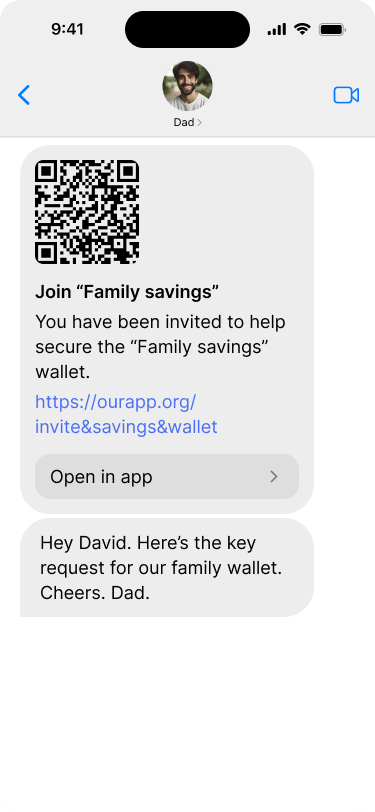
David receives the key request from his father in a text message.
Our app opens an loads the wallet configuration. If David hadn’t already installed the app, he would be taken to the app store to download it.
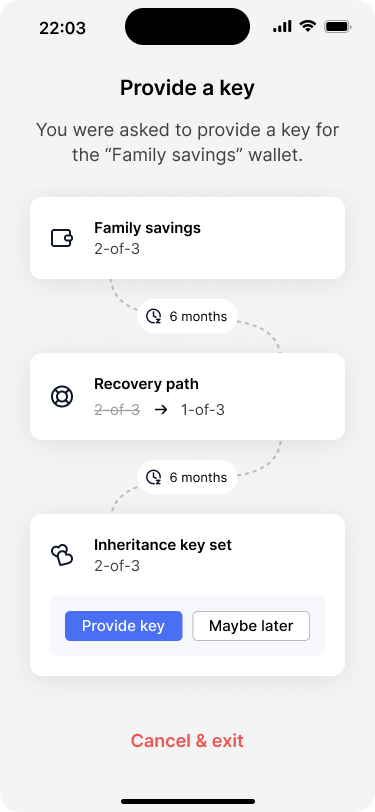
The wallet overview screen shows that David’s key will be part of the inheritance key set.
David goes through the key import flow.
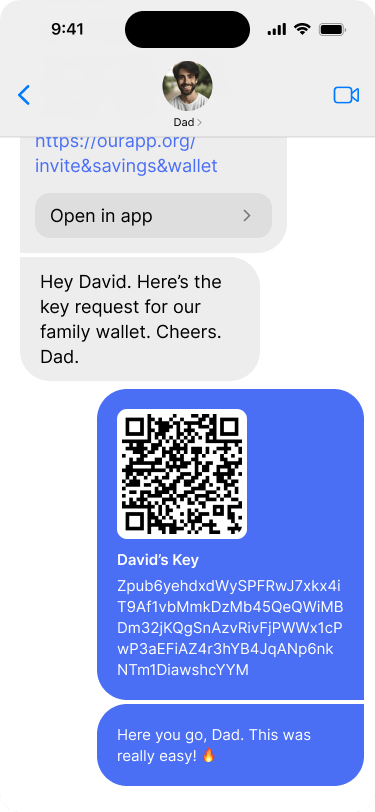
As soon as he has his key, David sends it via direct message back to his father.
Step 3: Finalizing the wallet #
After all of the keys have been added, Bob can proceed to create the wallet. They review the details and hit “create wallet”.
On the confirmation screen, he is asked to download the wallet backup kit. The couple doesn’t want to deal with the backup right now, so they decide to skip it. After all, there are no funds in the wallet yet.
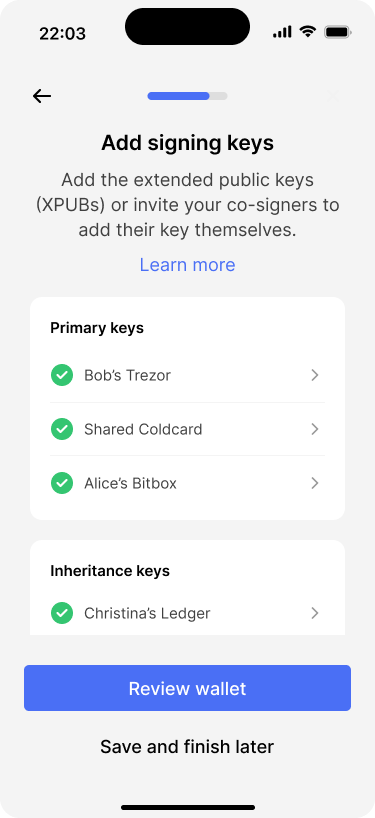
Bob sees that all six keys have been added.
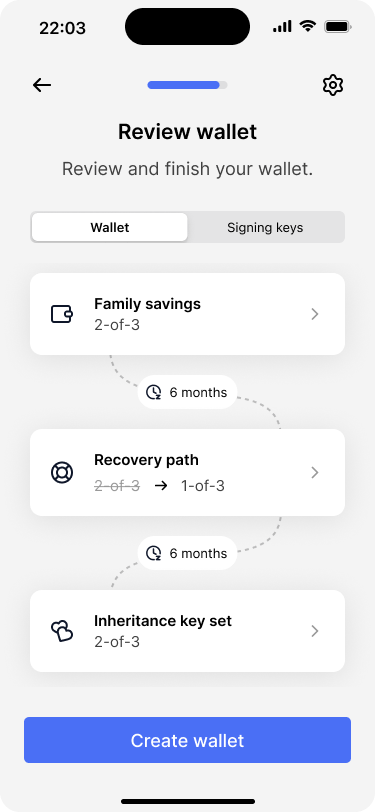
The review screen shows the complete wallet configuration. There is also a tab that contains the list of all keys.
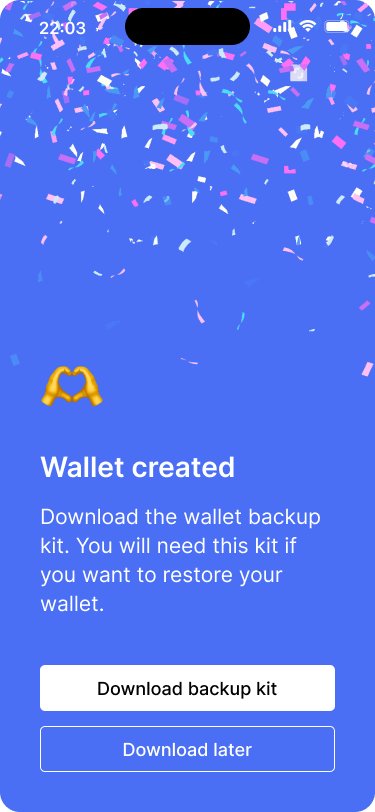
On the success screen, Bob gets prompted to download the wallet backup kit.
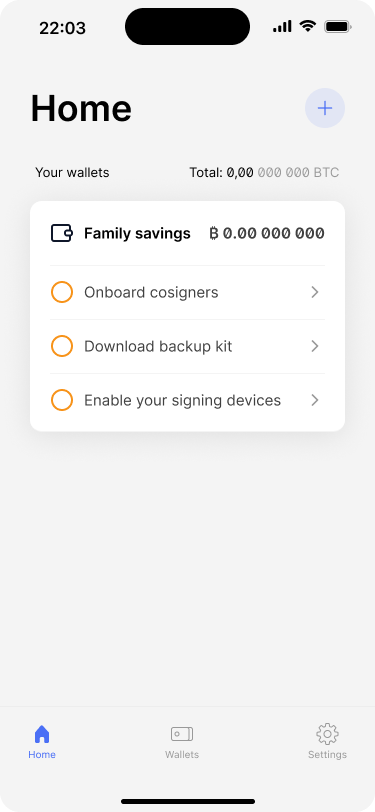
Bob and Alice can start using their new family savings wallet.
The homescreen shows the newly created wallet. In addition, the app shows a couple of reminders that they should still download the backup as well as scheduling a regular key check.